wireguard(6)应用synology和mac通信
目的
synology nas上部署wireguard当做server端,mac部署wireguard当做client端,实现网络互通。(远程访问私有nas资源/服务)
env
- synology-ds920+
- mac
- wireguard(p2p)
wireguard refer resouces
synology ds920+ (server)
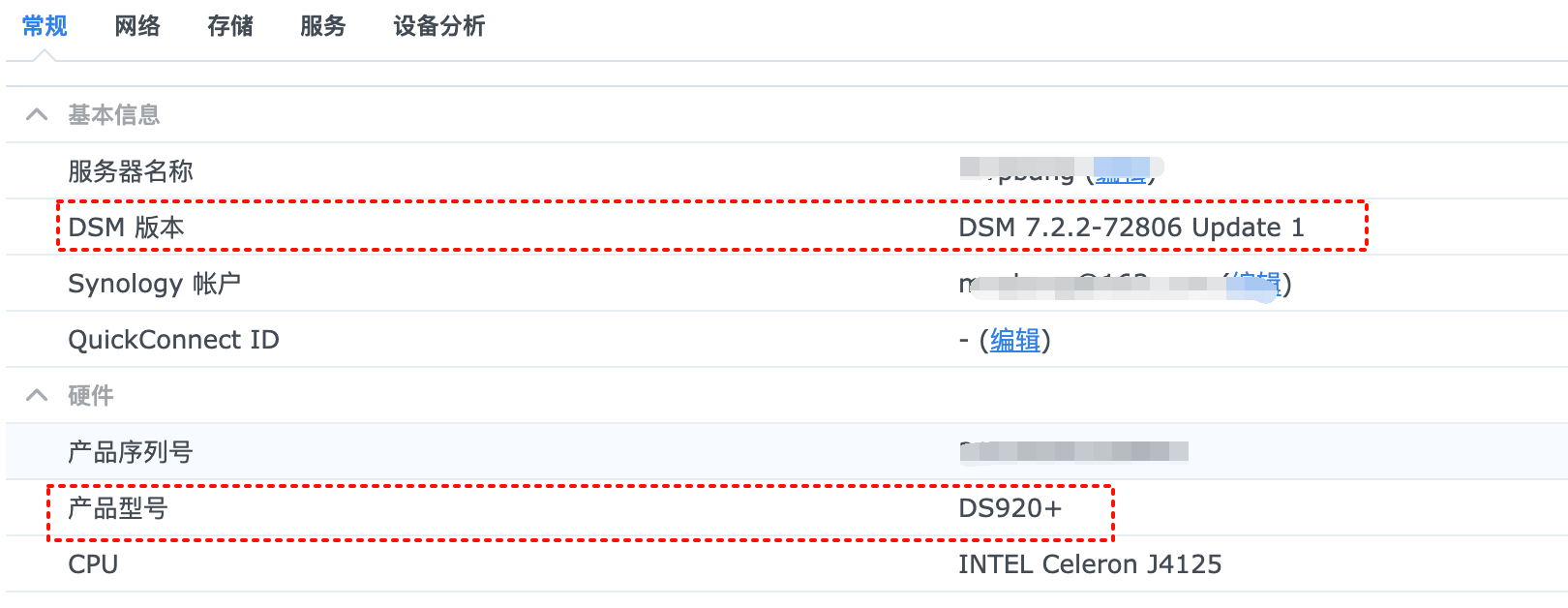
package arch: geminilake, dsm:7.2, ssh nas
wireguard-module-synology
1.下载spk
https://www.blackvoid.club/wireguard-spk-for-your-synology-nas/
https://github.com/vegardit/synology-wireguard/releases/tag/WireGuard-1.0.20220627-DSM7.2
2.安装spk
2.1基于套件中心安装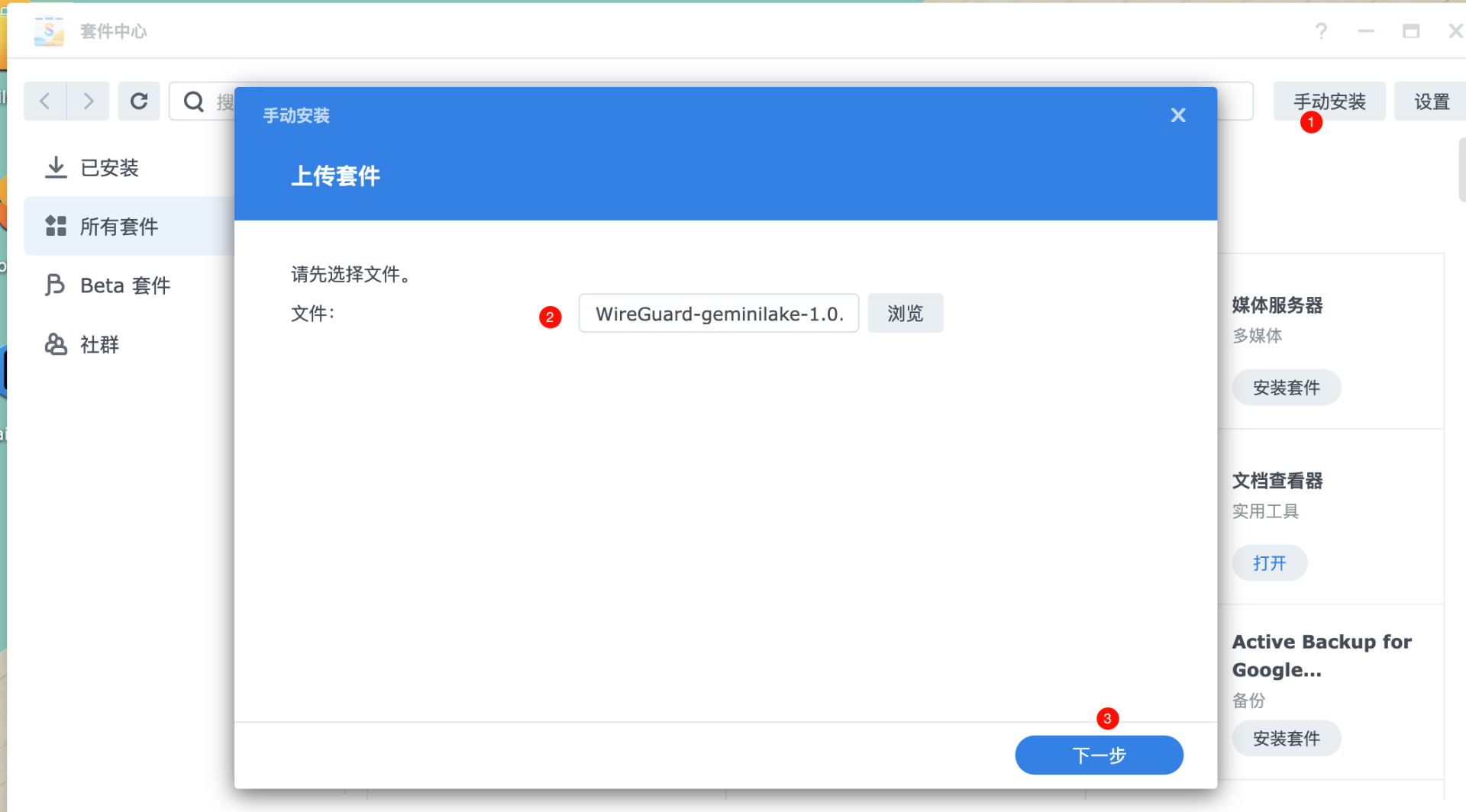
2.2基于命令行安装
sudo synopkg install WireGuard-geminilake-1.0.20220627_DSM7.2.spk
3.启动wireguard服务
# 启动
sudo /var/packages/WireGuard/scripts/start
# 关闭
sudo /var/packages/WireGuard/scripts/start-stop-status
4.基于wg-quick配置
4.1准备工作
1.创建目录
mkdir /etc/wireguard/
touch /etc/wireguard/wg0.conf
2.生成私钥、公钥
cd /etc/wireguard/
# server/client privatekey
wg genkey >sprivatekey
wg genkey >cprivatekey
# server/client publickey
wg pubkey <sprivatekey >spublickey
wg pubkey <cprivatekey >cpublickey
4.2wg0.conf配置
/etc/wireguard/wg0.conf
1 | [Interface] |
xxx -> sprivatekey, yyy -> cpublickey
5.管理wg服务
# 启动
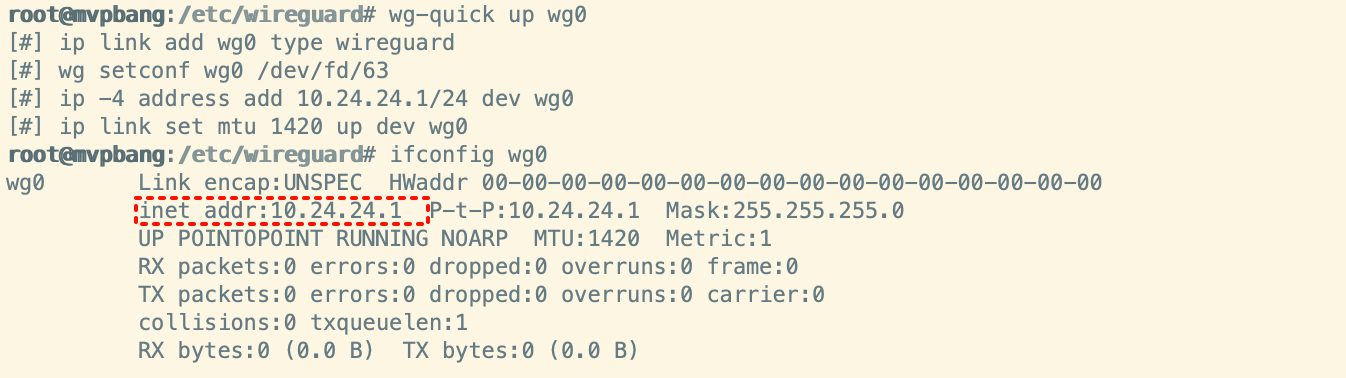
wg-quick up wg0
# 停止
wg-quick down wg0
# 查看wg状态
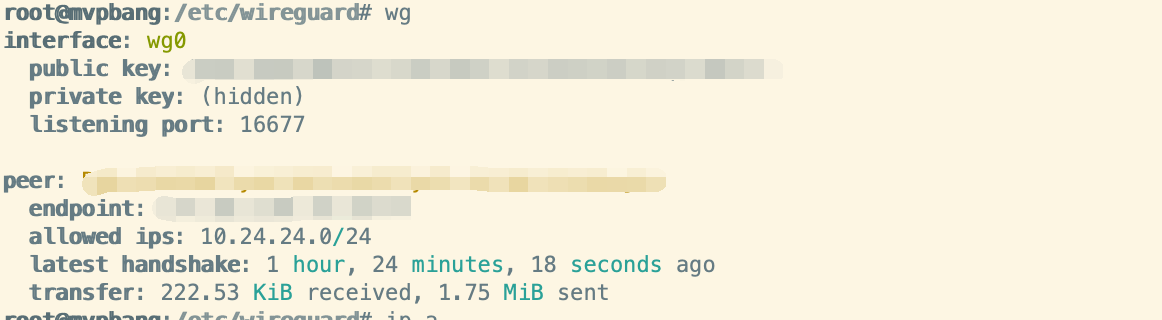
wg show
# wg0 enable autostart
sudo wg-autostart enable wg0
# wg0 disable autostart
sudo wg-autostart disable wg0
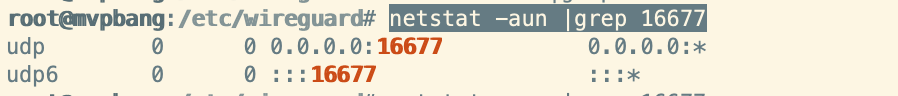
# check wireguard listen statue
netstat -aun |grep 16677
listen for udp protocol

6.synology上配置
目的:暴漏wireguard服务在互联网上,方便client建立隧道通信。
6.1配置ddns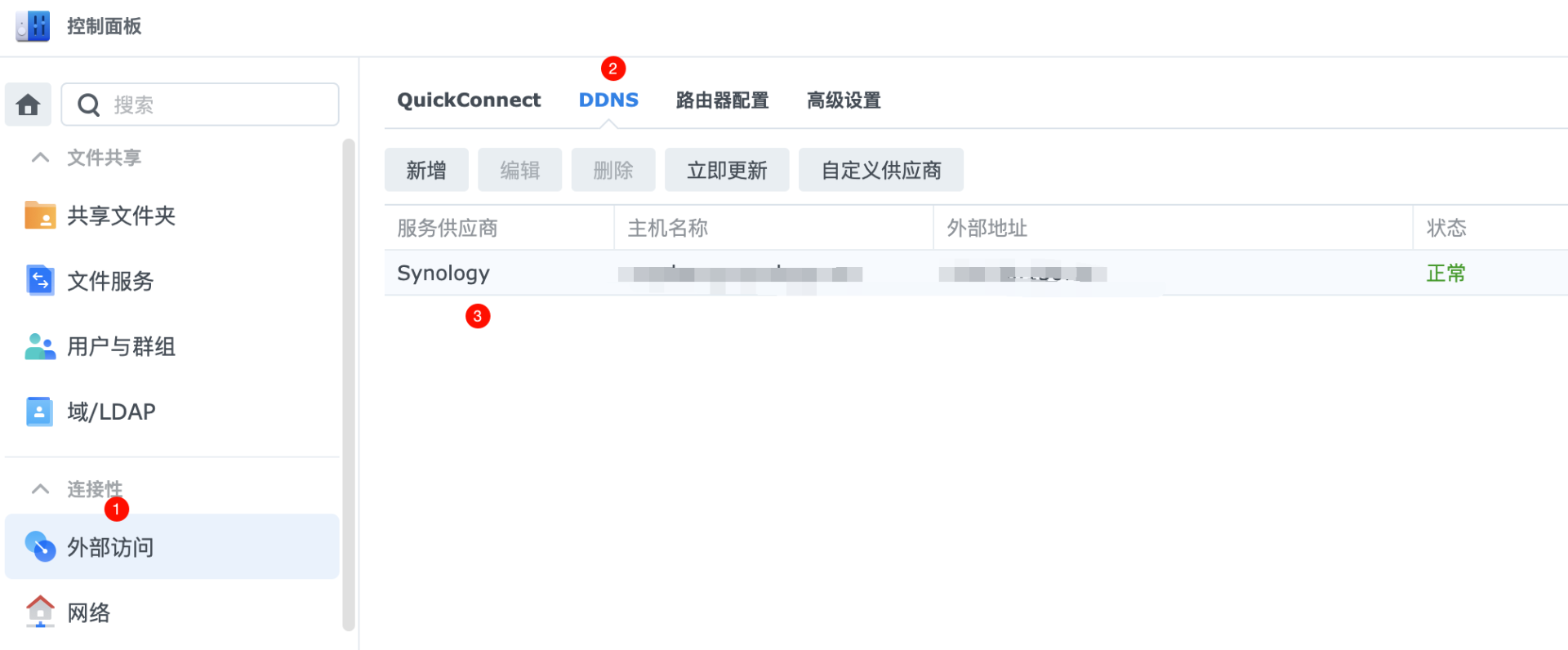
6.2路由器端口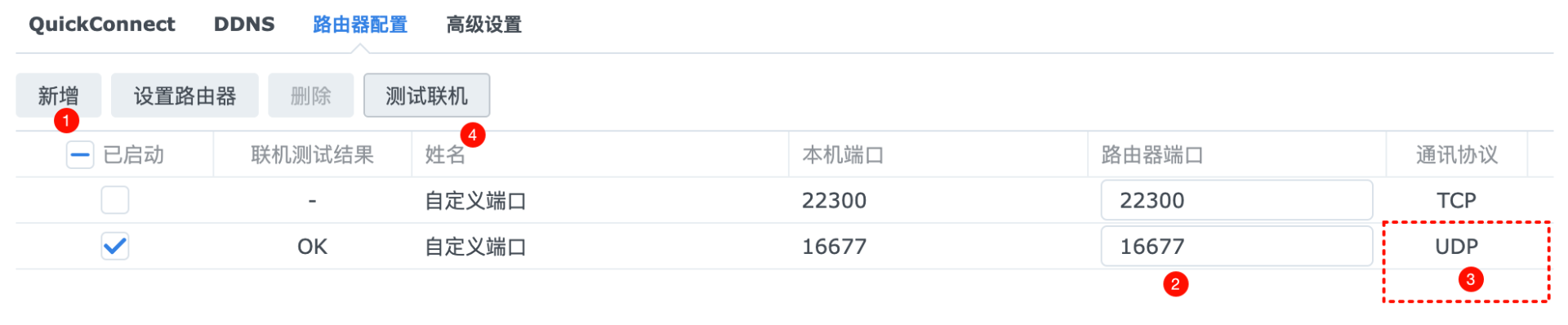
如果主路由器配置upnp则自动添加映射
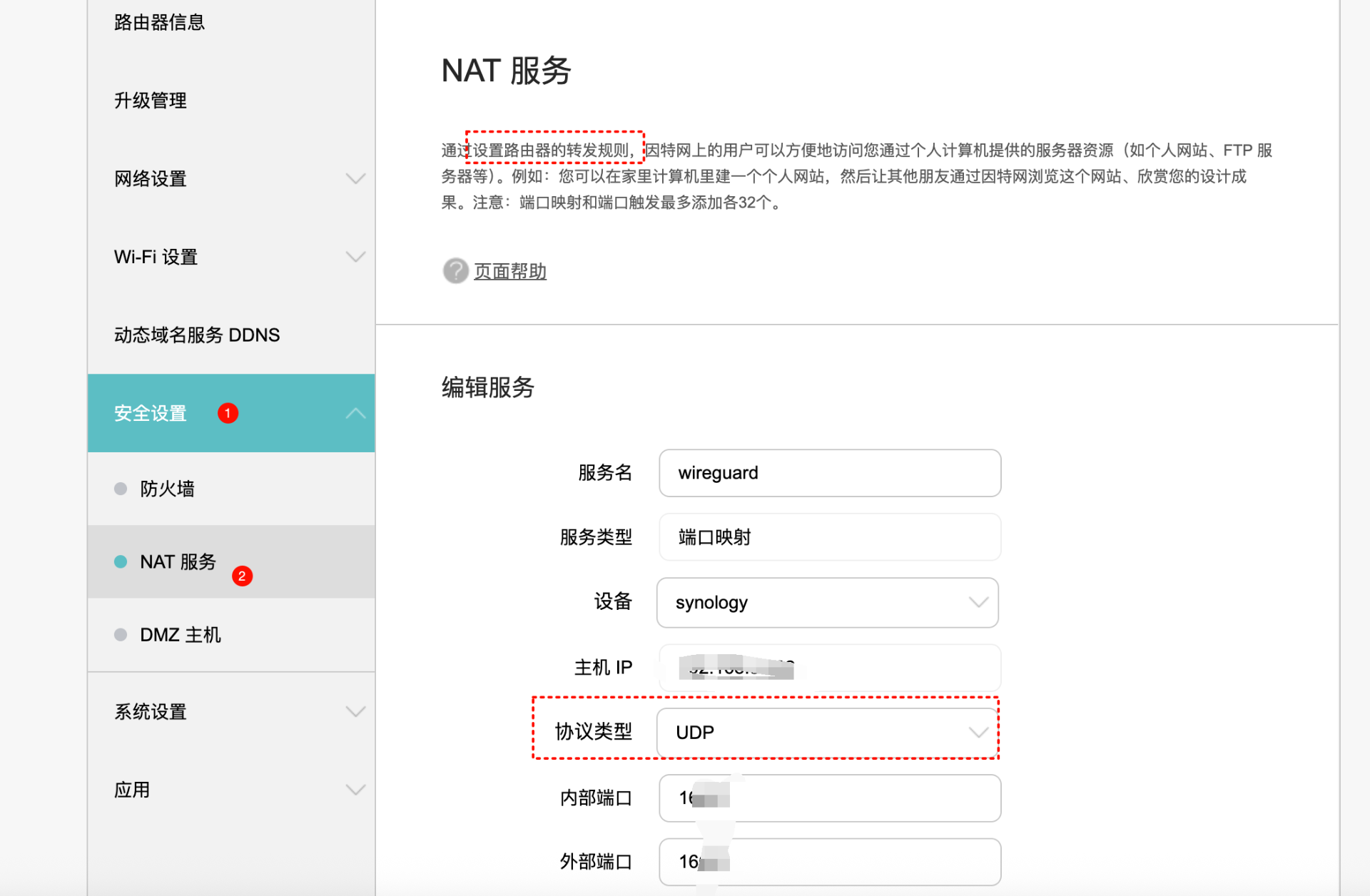
7.路由器设置(暴露端口)
7.1主路由器上映射wireguard udp端口
dmz主机
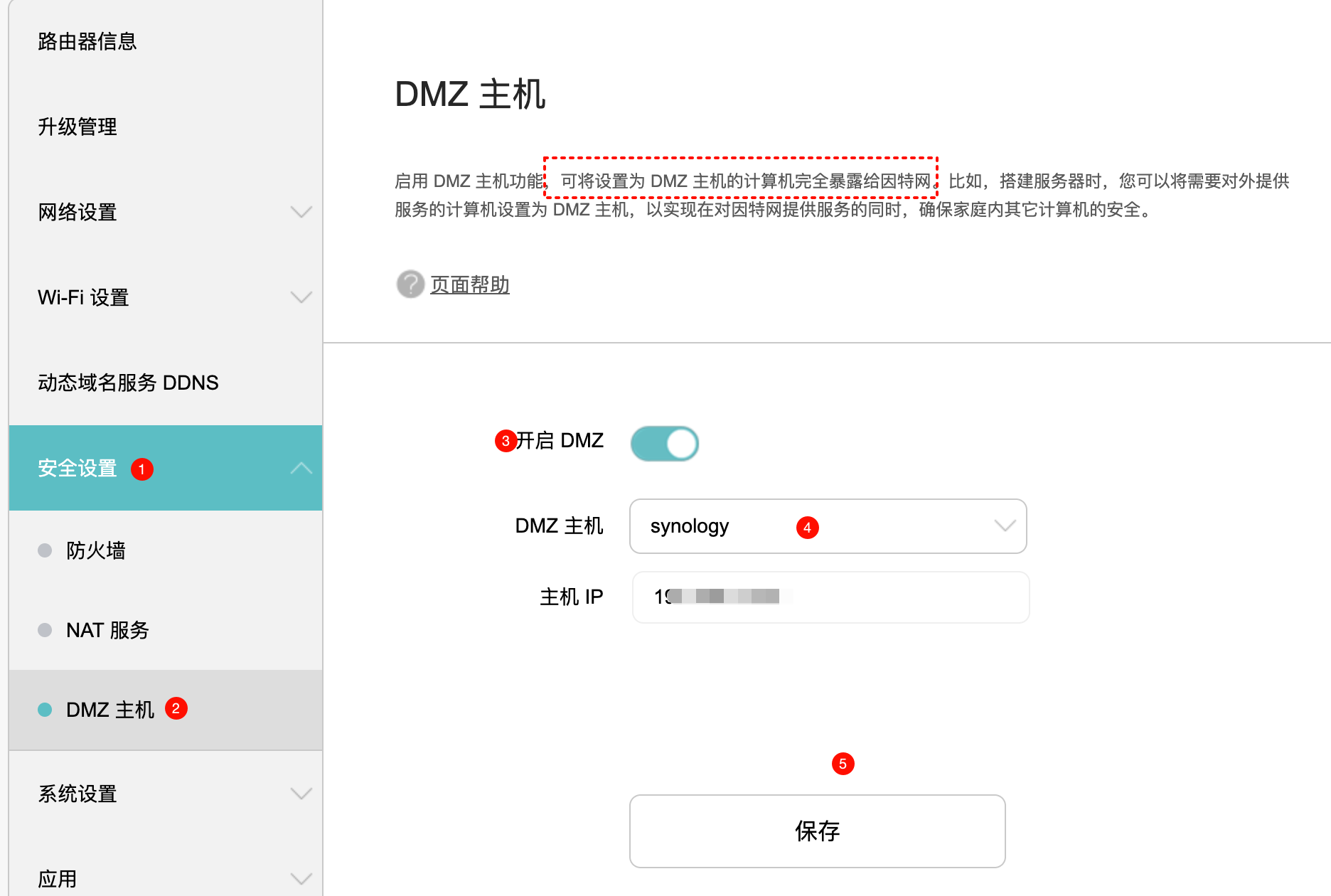
开启UPNP
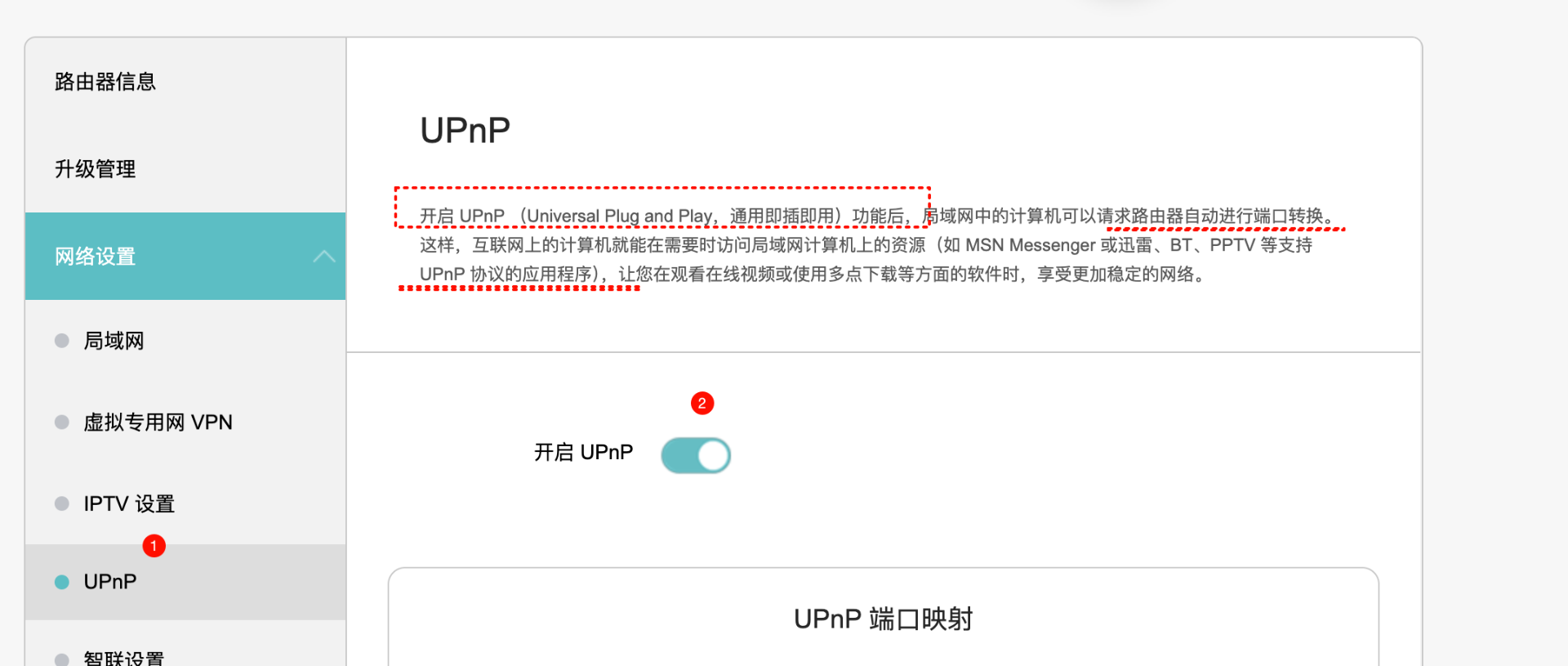
端口转发(更加安全)
mac(client)
1.安装wireguard关联包
brew install wireguard-go wireguard-tools
检测utun虚拟网卡占用情况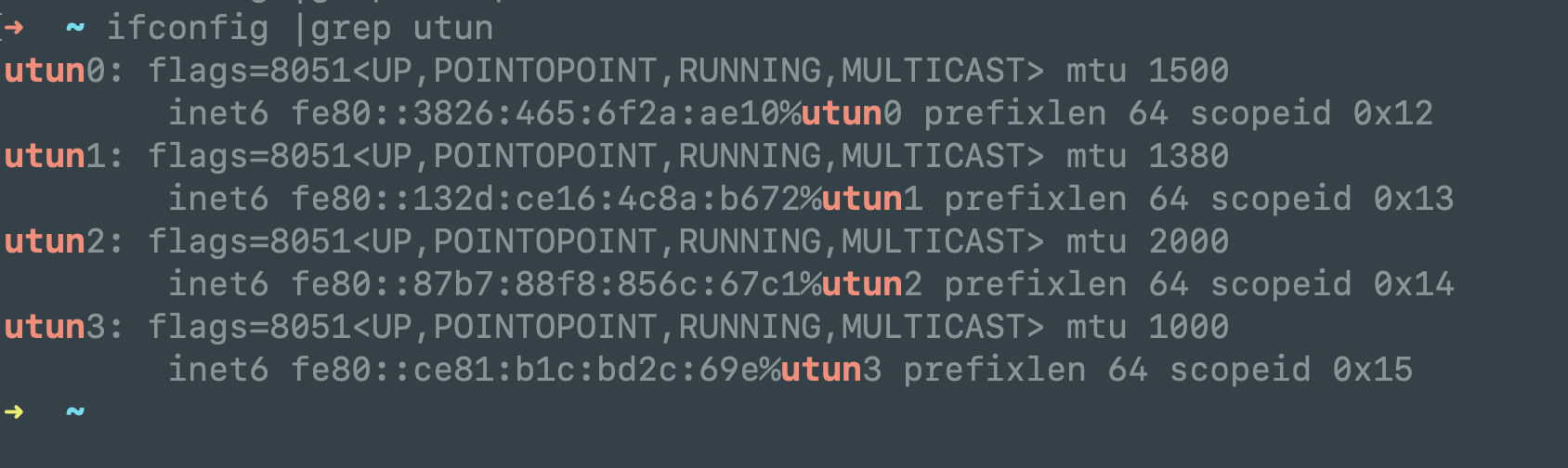
2.配置uputu.conf
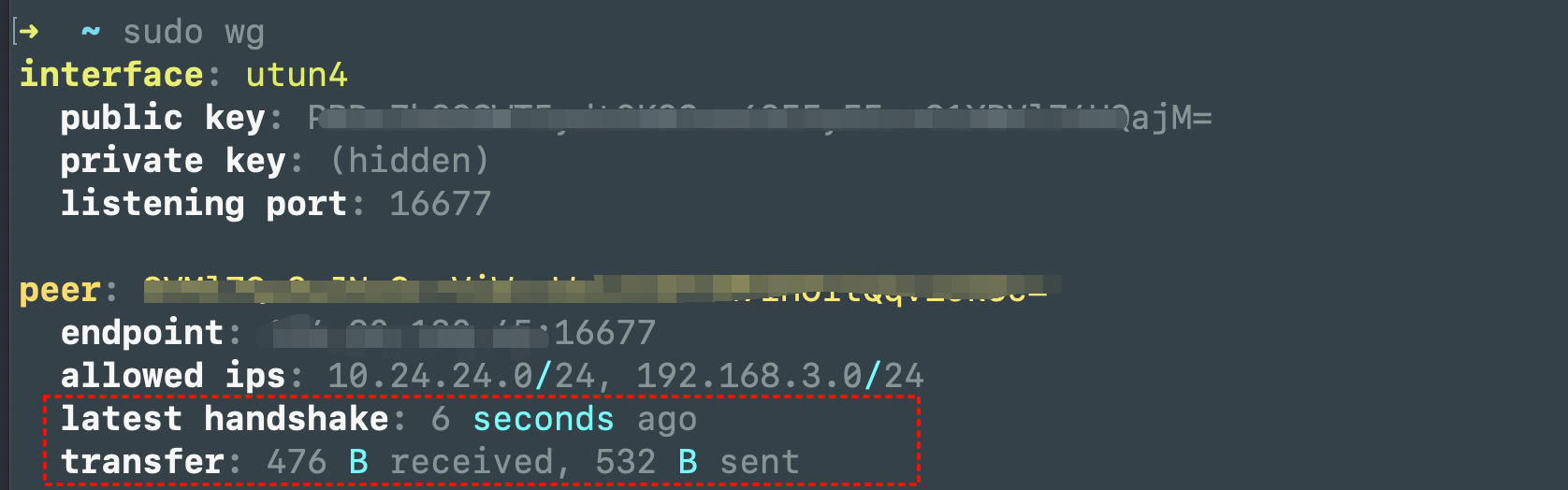
➜ ~ cat /etc/wireguard/utun4.conf
[Interface]
Address = 10.24.24.2
ListenPort = 16677
PrivateKey = xxx
[Peer]
PublicKey = yyy
AllowedIPs = 10.24.24.0/24, 192.168.3.0/24
Endpoint = zzz:16677
xxx 客户端私钥,yyy服务端公钥,zzz服务端暴漏在公网地址
3.启动wg-quick
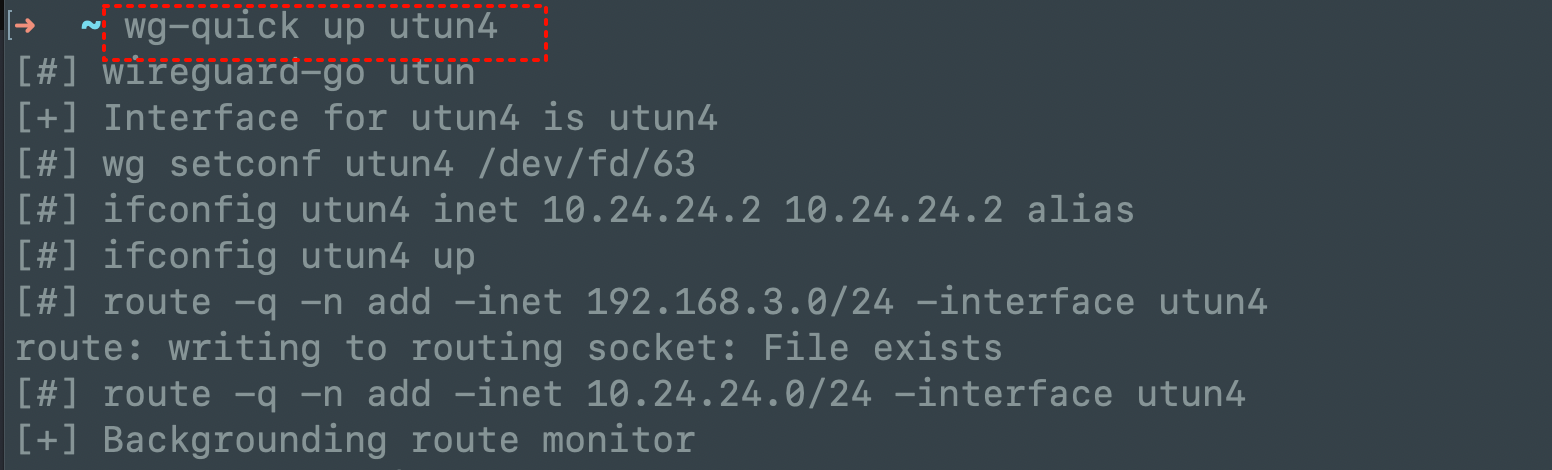
3.1快速启动wg-quick up/down utun4
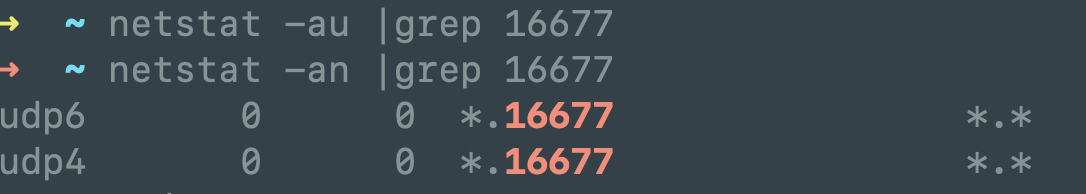
3.2检查client监听udp情况netstat -an |grep 16677
3.3ping serverping 10.24.24.1
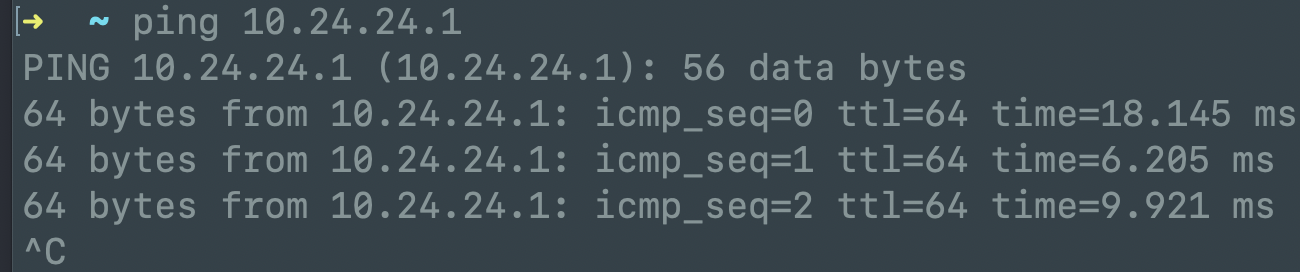
3.4查看配置及设备信息sudo wg